Advanced C2 Infrastructure Design: Building Resilient Red Team Operations
In today’s sophisticated threat landscape, red team operations require increasingly complex and resilient Command and Control (C2) infrastructures to successfully emulate advanced persistent threats. As blue teams implement more sophisticated detection mechanisms, red teamers must evolve their C2 design to maintain operational security while achieving their assessment objectives. This article explores advanced C2 infrastructure design patterns, implementation techniques, and operational considerations essential for modern red team engagements.
Understanding C2 Infrastructure Requirements
The primary goal of a C2 infrastructure is to establish and maintain secure, covert communication channels between compromised endpoints and operator-controlled servers. Modern C2 infrastructures must satisfy several key requirements:
- Resilience against detection by network security monitoring tools
- Multiple communication paths to ensure operational continuity
- Flexible protocol support to adapt to network environments
- Traffic blending capabilities to mimic legitimate network traffic
- Operational security to protect the identity and location of operators
The failure to meet any of these requirements can result in premature detection, allowing defenders to contain the simulated breach and nullify the effectiveness of the assessment.
Advanced C2 Architecture Models
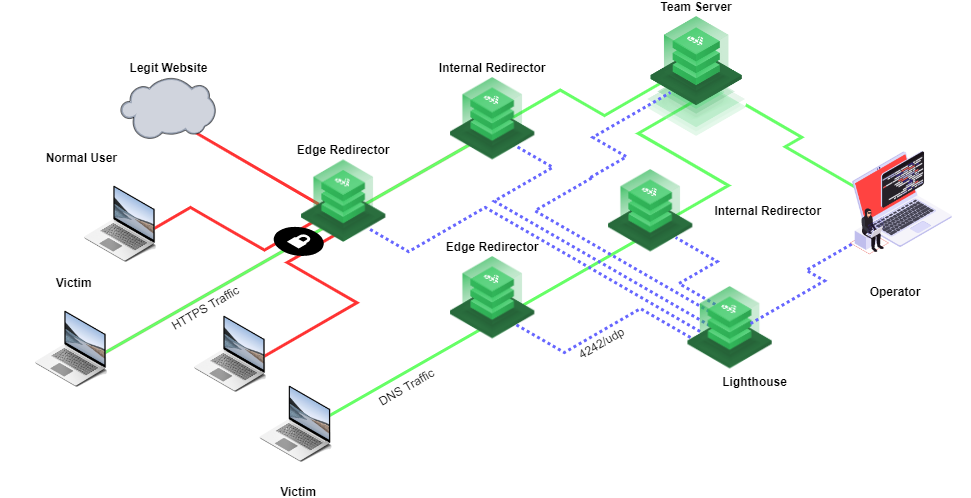
The Redirector Pattern
The foundation of sophisticated C2 infrastructures is the redirector pattern, which creates layers of abstraction between compromised hosts and the actual C2 server. A well-designed redirector pattern typically includes:
- Edge nodes: Front-facing servers that accept initial connections from compromised systems
- Transport nodes: Intermediate servers that relay traffic through varying protocols
- Team servers: Backend infrastructure running the actual C2 framework
This separation provides several advantages:
- If an edge node is discovered, the core C2 infrastructure remains protected
- Traffic can be filtered at multiple points to ensure only legitimate C2 traffic reaches team servers
- Different protocols and authentication mechanisms can be implemented at each layer
Compromised Host → Edge Redirectors → Transport Nodes → Team Server
Domain Fronting and CDN Utilization
Domain fronting remains a powerful technique for disguising C2 traffic, despite some CDN providers implementing countermeasures. By leveraging trusted domains through their CDN infrastructure, red teams can make C2 traffic appear to communicate with legitimate services.
Modern implementations often combine domain fronting with jitter, malleable profiles, and traffic shaping to further obfuscate the true nature of the communication.
Multi-tier Redirector Chains
Building on the basic redirector pattern, advanced C2 infrastructures implement multi-tier redirector chains with specialized functions:
- HTTPS redirectors: Primary ingress points using standard web protocols
- DNS redirectors: Alternative communication channels using DNS queries
- SMB redirectors: Internal network communication channels
- Custom protocol redirectors: Specialized channels for challenging environments
Each redirector type requires specific configuration and hardening to prevent detection while maintaining operational reliability.
Implementing Advanced C2 Components
Domain Infrastructure Design
Domain selection and management is critical for long-term C2 operations. Best practices include:
- Strategic domain selection: Choose domains that blend with the target environment's normal traffic patterns
- Domain aging: Register domains well in advance of operations to build reputation
- Domain categorization: Work with categorization services to place domains in appropriate business categories
- Certificate management: Implement proper SSL/TLS certificates that withstand scrutiny
A strategic approach to domain management involves creating multiple categories of domains:
- Long-term infrastructure domains: Used for core C2 components
- Short-term operational domains: Used for specific phases of an engagement
- Fallback domains: Activated only if primary infrastructure is compromised
Traffic Manipulation Techniques
Modern network traffic analysis tools have become increasingly effective at identifying anomalous patterns associated with C2 communications. Advanced red teams counter this using:
- Malleable C2 profiles: Customized traffic patterns that mimic legitimate applications
- Protocol obfuscation: Techniques to disguise the underlying C2 protocol
- HTTPS inspection bypass: Methods to evade SSL/TLS inspection
- Traffic timing manipulation: Irregular communication intervals to avoid timing-based detection
- Data chunking: Breaking communications into smaller, less-detectable fragments
In environments with sophisticated monitoring, combining these techniques becomes essential for maintaining persistent access.
Load Balancing and Redundancy
Operational resilience requires implementing proper load balancing and redundancy across the C2 infrastructure:
- Geographic distribution: Deploy components across multiple regions
- Provider diversity: Utilize multiple cloud service providers
- Automatic failover: Implement systems that detect and respond to component failure
- Dynamic infrastructure: Use infrastructure-as-code to rapidly deploy new components
These measures ensure that the compromise of individual C2 components doesn't jeopardize the entire operation.
Operational Security Considerations
Infrastructure Attribution Protection
Protecting against attribution is crucial for maintaining operational security. Key practices include:
- Anonymous acquisition: Use privacy-focused payment methods for infrastructure
- Compartmentalization: Separate infrastructure components logically and physically
- Exit node protection: Implement proper controls for operator access to prevent attribution
- Logging discipline: Maintain strict control over logs that could reveal operational patterns
- Infrastructure rotation: Regularly cycle through components to limit exposure
These practices help ensure that even if individual components are discovered, they can't be easily tied back to the red team.
Defense Against Counter-IR
Sophisticated defenders will attempt to investigate and counter red team infrastructure once detected. Planning for this includes:
- Canary tokens: Deploy monitoring mechanisms to detect blue team investigation
- Honeypot segments: Create deliberately discoverable components to distract from critical infrastructure
- Counter-response automation: Implement systems that react to detection attempts
Understanding how defenders respond to C2 discovery allows red teams to plan appropriate countermeasures and maintain operational capability.
Framework Selection and Customization
Modern C2 Frameworks
Several C2 frameworks have emerged as industry standards, each with different strengths:
- Cobalt Strike: The industry standard with extensive features but high detection rates
- Covenant: Modern .NET-based framework with built-in evasion capabilities
- Sliver: Go-based framework designed for extended operations
- Mythic: Modular framework supporting diverse agents and communication methods
- Havoc: Newer framework designed with evasion as a primary goal
The selection of a framework should be based on the specific requirements of the engagement, target environment, and red team capabilities.
Framework Modification and OPSEC
Using publicly available C2 frameworks presents significant risks as defenders actively develop signatures for these tools. Advanced red teams address this by:
- Customizing framework code: Modifying source code to change detectable patterns
- Developing custom modules: Creating specialized functionality that isn't in public repositories
- Implementing unique obfuscation: Applying organization-specific obfuscation techniques
- Regular signature testing: Continuously testing against updated EDR solutions
Building Custom Protocol Handlers
For the most sophisticated operations, developing custom protocol handlers provides significant advantages:
- Unique traffic patterns that don't match known C2 signatures
- Environment-specific protocols designed for the target network
- Custom encryption that evades standard inspection techniques
While resource-intensive, custom protocol development represents the highest level of C2 sophistication.
Detection Evasion Strategies
Endpoint Evasion Techniques
Modern Endpoint Detection and Response (EDR) systems present significant challenges for maintaining persistent access. Advanced techniques include:
- In-memory operation: Minimizing disk artifacts through memory-resident execution
- Direct syscall implementation: Bypassing API monitoring hooks
- AMSI/ETW bypass methods: Evading Microsoft's detection mechanisms
- Signed binary abuse: Leveraging trusted applications for malicious actions
- EDR sensor tampering: Techniques to weaken or disable endpoint protections
These techniques must be combined and customized based on the specific EDR solution deployed in the target environment.
Network-level Evasion
At the network level, red teams must implement comprehensive evasion strategies:
- DPI evasion: Techniques to bypass deep packet inspection
- Protocol tunneling: Encapsulating C2 traffic within legitimate protocols
- Traffic pattern normalization: Ensuring traffic patterns match legitimate applications
- Split-tunnel approaches: Dividing traffic across multiple channels to avoid pattern detection
- Legitimate service abuse: Leveraging trusted services for communication channels
Advanced penetration testing techniques often incorporate these network evasion approaches to maintain persistent access.
Case Study: Multilayer C2 in a Segmented Environment
Consider a red team engagement targeting a financial institution with highly segmented networks, multiple security solutions, and sophisticated monitoring. An effective C2 approach might include:
- Initial access via phishing with browser-based exploitation
- First-stage beacons communicating through domain fronting to external redirectors
- Internal pivot nodes using SMB relay techniques
- Separate C2 channels for different network segments
- Data exfiltration through encrypted DNS tunneling via dedicated infrastructure
This layered approach allows for persistent operation even if components are discovered, with each layer providing specific advantages for different network segments.
Testing and Validation
Red vs. Blue Exercises
Before deployment in actual assessments, comprehensive testing of C2 infrastructure is essential:
- Controlled exercises against modern security stacks
- Adversary emulation against your own infrastructure
- Detection tuning based on test results
- Evasion refinement to address identified weaknesses
Purple team exercises provide an ideal environment for testing and refining C2 infrastructure before actual client engagements.
Signature Analysis and Development
Proactive signature development helps identify potential detection issues:
- Capture traffic from your C2 infrastructure
- Analyze for unique patterns or indicators
- Develop signatures that would detect your own infrastructure
- Modify C2 components to evade these signatures
This continuous improvement cycle helps maintain the effectiveness of C2 infrastructure against evolving detection capabilities.
Documentation and Operational Procedures
Infrastructure Documentation
Proper documentation is critical for complex C2 infrastructures:
- Network diagrams showing all components and traffic flows
- Configuration details for each component
- Access credentials stored securely
- Recovery procedures for various failure scenarios
- Rotation schedules for infrastructure components
This documentation ensures operational continuity and enables rapid response to infrastructure issues.
Communication Security
Securing communications between red team members is as important as securing the C2 infrastructure itself:
- Encrypted communication channels for team coordination
- Out-of-band signaling for critical notifications
- Emergency shutdown procedures that can be triggered securely
- Authentication processes for team member verification
These measures protect both the operation and the operators from compromise.
Ethical and Legal Considerations
Any discussion of advanced C2 techniques must address ethical and legal considerations:
- Proper authorization through detailed scoping documents
- Data handling policies to protect sensitive information
- Activity boundaries clearly defined before operations begin
- Emergency contacts for both red and blue teams
- Proper deconfliction with security teams for critical systems
Professional red team operations always maintain strict adherence to ethical and legal boundaries while still providing realistic adversary emulation.
Conclusion
Building advanced C2 infrastructure requires deep technical knowledge, careful planning, and continuous adaptation. As detection technologies evolve, so too must the techniques used to establish and maintain covert communication channels. The most effective red teams approach C2 design as an ongoing process of improvement rather than a one-time implementation.
By implementing the layered redirector patterns, traffic manipulation techniques, and operational security measures outlined in this article, red teams can build resilient C2 infrastructures capable of supporting sophisticated adversary emulation scenarios. This allows for more realistic assessments that help organizations better prepare for actual threats they may face.
For organizations looking to enhance their detection capabilities, understanding these advanced C2 techniques provides valuable insights into the methods used by sophisticated adversaries. The cat-and-mouse game between attackers and defenders continues to drive innovation on both sides of the security equation.
Implementing proper threat hunting techniques and SOC operations to detect these advanced C2 methods represents the cutting edge of defensive security.




