Advanced Process Hollowing Detection: Identifying and Countering Memory Injection Techniques
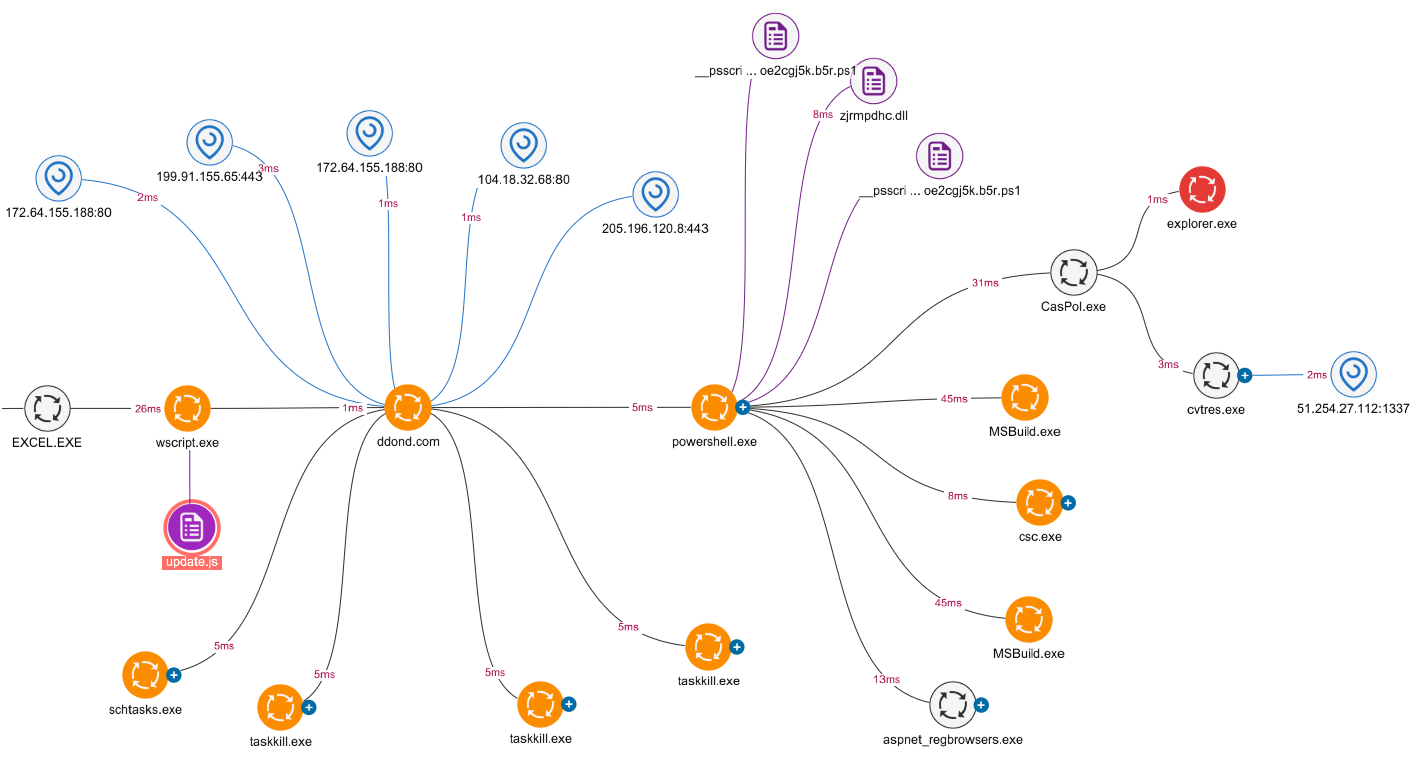
In the evolving landscape of cyber threats, attackers continuously refine their techniques to evade detection and establish persistence on compromised systems. Process hollowing has emerged as a particularly insidious method used by sophisticated malware and advanced persistent threats (APTs) to conceal malicious code execution within seemingly legitimate processes. This technique allows attackers to operate beneath the radar of many traditional security controls, making it a persistent challenge for security teams.
Understanding Process Hollowing: The Attacker's Perspective
Before diving into detection strategies, it's crucial to understand how process hollowing works at a technical level. Process hollowing (also known as process replacement or RunPE) is a memory injection technique where an attacker creates a legitimate process in a suspended state, hollows out its memory, and replaces it with malicious code.
The Process Hollowing Technique
The typical process hollowing attack follows these steps:
- Process Creation: The attacker creates a legitimate process (often a system process like
svchost.exe,explorer.exe, orregsvr32.exe) in a suspended state using theCreateProcessAPI with theCREATE_SUSPENDEDflag. - Memory Unmapping: The original executable image is unmapped from memory using functions like
ZwUnmapViewOfSectionorNtUnmapViewOfSection. - Memory Allocation: New memory is allocated within the process using
VirtualAllocExwith executable permissions. - Code Injection: The malicious payload is written into the newly allocated memory space using
WriteProcessMemory. - Entry Point Modification: The process's thread context is modified to point to the malicious code entry point using
SetThreadContext. - Process Resumption: The suspended process is resumed with
ResumeThread, executing the malicious code under the guise of the legitimate process.
This technique proves effective because the process appears legitimate in task managers and process lists, showing the original file path and expected attributes despite executing entirely different code. According to recent research in malware evasion techniques, process hollowing has been observed in numerous malware families, including Dridex, Emotet, and various ransomware strains.
Detection Challenges and Approaches
Detecting process hollowing presents several unique challenges for security teams:
Challenge 1: Legitimate vs. Malicious Use
Process hollowing techniques occasionally appear in legitimate software. Some security products, game launchers, and application protection systems use similar techniques for anti-piracy or anti-debugging purposes.
Detection Approach: Context-based analysis is essential - examining the process lineage, user context, timing, and associated behaviors helps differentiate legitimate from malicious uses.
Challenge 2: Variations in Implementation
Attackers continuously modify the basic process hollowing technique to evade detection:
- Section remapping instead of complete unmapping
- Direct modification of the Process Environment Block (PEB)
- Partial hollowing where only specific sections are replaced
- Living-off-the-land approaches that leverage legitimate system calls
Detection Approach: Focus on fundamental artifacts that remain consistent across variations rather than specific API call patterns.
Challenge 3: Anti-forensic Techniques
Advanced implementations incorporate anti-forensic techniques:
- Memory region permission manipulation
- Timestomping of memory artifacts
- Selective execution based on environment checks
- Thread context manipulation to hide execution flow
Detection Approach: Implement comprehensive memory scanning and behavioral analysis that examines multiple indicators rather than relying on single detection points.
Effective Detection Strategies
A multi-layered approach provides the most effective detection of process hollowing techniques. Here are the key strategies security teams should implement:
1. Memory Forensics and Scanning
Memory-focused detection provides the most reliable identification of process hollowing:
Memory Mapping Analysis:
- Look for discrepancies between memory-mapped content and the corresponding file on disk
- Identify mapped sections with unexpected permissions (particularly executable sections that don't match the original binary)
- Detect unmapped sections that should exist in legitimate processes
PE Header Examination:
- Validate PE headers in memory against the original file
- Check for manipulated entry points
- Identify inconsistencies in the Import Address Table (IAT)
- Detect modifications to the Process Environment Block (PEB)
Implementation Example:
# PowerShell example using Get-InjectedThread.ps1 to detect memory anomalies
Import-Module .\Get-InjectedThread.ps1
Get-InjectedThread | Where-Object {$_.StartAddress -notmatch $_.PathToFile}
Memory scanning tools like Volatility, Rekall, and specialized EDR solutions can automate many of these checks. For example, Volatility's malfind plugin identifies process sections with suspicious memory permissions and characteristics.
2. Behavioral Analysis and API Monitoring
Monitoring system behavior and suspicious API call patterns can identify process hollowing attempts in progress:
Critical API Sequences:
Monitor for suspicious sequences of API calls indicating process hollowing:
CreateProcesswithCREATE_SUSPENDEDflagNtUnmapViewOfSection/ZwUnmapViewOfSectioncallsVirtualAllocExwithPAGE_EXECUTE_READWRITEpermissionsWriteProcessMemoryoperationsSetThreadContextfollowed byResumeThread
Parent-Child Process Relationships:
- Unusual parent-child process relationships (e.g.,
explorer.exespawningsvchost.exe) - Creation of common target processes (like
svchost.exe) from unexpected parents - Multiple suspended process creations in rapid succession
The MITRE ATT&CK framework classifies process hollowing as a sub-technique of process injection (T1055.012) and provides additional behavioral indicators to monitor.
3. Integrity Verification
Verifying the integrity of running processes can identify hollowed processes:
Memory-to-Disk Comparison:
- Calculate hashes of memory-resident code and compare with on-disk executable
- Validate digital signatures of memory sections against expected values
- Check for tampered entry points and execution flows
Code Flow Analysis:
- Analyze execution flow for unexpected transitions
- Identify JMP/CALL instructions to unusual memory regions
- Look for shellcode characteristics in process memory
According to research on advanced threat detection, integrating memory integrity verification into regular security operations significantly improves the detection of memory manipulation techniques.
4. Event Correlation and Context Analysis
Correlating multiple events provides a more complete picture that reduces false positives:
Process Timing Analysis:
- Brief suspended states followed by unexpected behavior
- Unusual delays between process creation and actual execution
- Processes that immediately establish network connections after a suspended state
Resource Access Patterns:
- Unexpected network connections from recently created processes
- Access to sensitive registry keys or files inconsistent with the original process purpose
- Unusual DLL loading patterns after process initialization
Implementation Example:
# YARA rule example for detecting potential process hollowing artifacts
rule Detect_Process_Hollowing {
meta:
description = "Detects potential process hollowing in memory"
author = "PwnVector Research Team"
reference = "Internal Research"
strings:
$create_process = "CreateProcessW" wide ascii
$virtual_alloc = "VirtualAllocEx" wide ascii
$write_memory = "WriteProcessMemory" wide ascii
$set_context = "SetThreadContext" wide ascii
$resume_thread = "ResumeThread" wide ascii
$unmap_section = "NtUnmapViewOfSection" wide ascii
condition:
($create_process and $virtual_alloc and $write_memory and
$set_context and $resume_thread) or $unmap_section
}
5. Advanced EDR and XDR Integration
Modern Endpoint Detection and Response (EDR) and Extended Detection and Response (XDR) platforms provide integrated capabilities for detecting process hollowing:
Real-time Monitoring:
- Continuous scanning for memory discrepancies
- Behavioral baselining to identify unusual process activities
- Integration with threat intelligence to identify known malicious patterns
Response Automation:
- Automatic memory dumps of suspicious processes
- Process isolation upon detection of hollowing indicators
- Forensic data collection for further analysis
Leading EDR solutions implement multiple detection layers for process hollowing and other memory injection techniques.
Implementing Detection in Enterprise Environments
Successfully detecting process hollowing in enterprise environments requires a systematic approach:
1. Baseline Legitimate Behavior
Before implementing detection controls:
- Document legitimate software that uses memory manipulation techniques
- Establish baseline behavior for common system processes
- Identify normal parent-child process relationships
- Map expected memory access patterns for critical applications
2. Defense-in-Depth Architecture
Implement multiple detection layers:
- Kernel-level monitoring: Track memory operations and process creation
- User-mode hooks: Monitor API calls associated with process hollowing
- Memory scanning: Regular scans for memory inconsistencies
- Behavioral analysis: Identify unusual patterns indicative of hollowing
3. SOC Integration and Workflow
Integrate process hollowing detection into Security Operations Center (SOC) workflows:
- Develop specific alert triage procedures for process hollowing detections
- Create investigation playbooks for memory injection techniques
- Establish escalation paths based on confidence levels
- Implement regular testing of detection capabilities
4. Regular Testing and Validation
Validate detection capabilities through regular testing:
- Conduct simulated process hollowing attacks using red team exercises
- Test detection across different OS versions and configurations
- Validate detection of known variants and custom implementations
- Review and update detection rules based on effectiveness
Case Study: Detecting Process Hollowing in Active Attacks
To illustrate effective detection in practice, consider this real-world case study:
Detection Scenario: Emotet Malware Using Process Hollowing
In a recent incident response engagement, process hollowing was used by Emotet malware to hide its execution:
- Initial Detection: An EDR alert indicated a suspicious pattern of API calls from a legitimate
explorer.exeprocess creating a suspendedsvchost.exeprocess. - Memory Analysis: Memory scanning revealed discrepancies between the on-disk
svchost.exebinary and its memory-resident code. The PE header in memory had been modified, and several sections had unexpected execution permissions. - Behavioral Confirmation: The hollowed process attempted to establish communication with known command and control servers, confirming the malicious nature of the activity.
- Root Cause Analysis: Investigation revealed an initial compromise through a phishing email with a malicious Office document that exploited a macro vulnerability.
- Containment: The security team isolated affected systems, collected memory images for forensic analysis, and implemented specific detection rules based on the observed techniques.
This case demonstrates the value of layered detection approaches that combine memory analysis, behavioral monitoring, and threat intelligence.
Advanced Detection Techniques
Beyond standard methods, several advanced techniques can enhance process hollowing detection:
1. Thread Execution Stack Analysis
Examining thread execution stacks can reveal anomalies associated with hollowed processes:
- Unusual return addresses pointing to dynamically allocated memory
- Missing stack frames that should appear in legitimate execution
- Evidence of stack manipulation techniques
Technical Implementation:
// Simplified C++ example for stack walking to identify anomalies
void AnalyzeThreadStacks(DWORD processId) {
HANDLE hProcess = OpenProcess(PROCESS_ALL_ACCESS, FALSE, processId);
HANDLE hThread = /* Get thread handle */;
CONTEXT context;
GetThreadContext(hThread, &context);
// Walk the stack and check for anomalies
DWORD64 stackAddress = context.Rsp;
// Analyze stack frames for unexpected patterns
// Check return addresses against mapped module ranges
}
2. Hardware Performance Counter Analysis
Modern processors include performance monitoring counters (PMCs) that can detect certain hollowing behaviors:
- Abnormal instruction execution patterns
- Cache behavior inconsistent with legitimate processes
- Branch prediction anomalies associated with injected code
According to research on hardware-assisted security, PMCs can detect certain types of memory manipulation with minimal performance impact.
3. Memory Paging Analysis
Process hollowing often leaves artifacts in memory paging structures:
- Modified page table entries (PTEs) with unexpected attributes
- Unusual patterns of demand paging
- Inconsistent working set behaviors compared to legitimate processes
4. Code Flow Graph Analysis
Building and analyzing code flow graphs can identify hollowed processes:
- Unexpected control flow transitions
- Missing or modified function call patterns
- Evidence of code patching or hooking
Future Trends in Process Hollowing and Detection
As detection capabilities improve, attackers continue to evolve their techniques. Security teams should be aware of emerging trends:
Emerging Process Hollowing Variations
- Module hollowing: Similar to process hollowing but targets DLLs instead of executables
- Transactional hollowing: Uses the Transaction API to manipulate memory with better atomicity
- Dynamic forking techniques: Combines process hollowing with process forking to evade detection
- Reflective loading variations: Hybrids of reflective loading and process hollowing techniques
Advancing Detection Capabilities
- Machine learning-based detection: Using AI to identify subtle patterns associated with hollowing
- Runtime attestation: Cryptographic verification of code execution integrity
- Hardware-assisted monitoring: Leveraging CPU features like Intel PT (Processor Trace) for more accurate detection
- Hypervisor-level monitoring: Using virtualization-based security to detect memory manipulation
Conclusion
Process hollowing remains a powerful technique in the attacker's arsenal, providing an effective means to execute malicious code while evading many security controls. However, with a comprehensive detection strategy that leverages memory forensics, behavioral analysis, and advanced monitoring, security teams can significantly improve their ability to detect and respond to these threats.
Implementing the detection techniques outlined in this article should be part of a broader endpoint protection strategy. Organizations should ensure their security teams have the necessary tools, training, and processes to effectively identify and respond to process hollowing and other advanced memory manipulation techniques.
Remember that no single detection method is foolproof. A defense-in-depth approach that combines multiple detection layers provides the most effective protection against these sophisticated evasion techniques. By understanding how process hollowing works from an attacker's perspective, defenders can develop more effective countermeasures and continuously improve their detection capabilities.




