Comprehensive Guide to Active Directory Pentesting
Introduction
The world of cybersecurity is vast and complex, with numerous avenues to safeguard or exploit a network. One such avenue is the testing of Active Directory (AD) - a crucial component of network infrastructure. This article will delve into the detail of penetration testing or 'pentesting' of Active Directory services; a critical aspect of cybersecurity assessment. We will explore the nuances of AD pentesting, why it is a vital part of any robust cybersecurity strategy, and the potential risks if left unaddressed. For an overarching view of advanced threat hunting techniques, check out this article which covers an array of cybersecurity issues.
Technical Background
Active Directory (AD) is a Microsoft product that consists of several services to help manage a network's users and computers. It is a directory service for Windows domain networks and is involved in numerous aspects of network management, including managing user data, security, and distributed resources, and facilitating interoperability with other directories.
Evolution of Active Directory
Active Directory was first introduced with Windows 2000 Server edition and has evolved with each subsequent Windows Server release. Initially, its primary function was to provide central authentication and authorisation services for Windows-based computers. However, over the years, it has grown to support LDAP, the Internet standard for directory services.
Underlying Technical Mechanisms
At its core, AD operates under a hierarchical structure and uses a database to store all directory data. This database holds all the information about user accounts, computers, groups, and other objects. It also maintains information about the relationships between objects, the rules for object creation and configuration, and the schema that dictates the kinds of objects that can be stored.
In the context of pentesting, understanding the underlying mechanisms of AD is crucial. Follow the link to the Google Cloud Security page for a detailed discussion on cloud-based directory services, which are becoming increasingly popular.
Practical Implementation
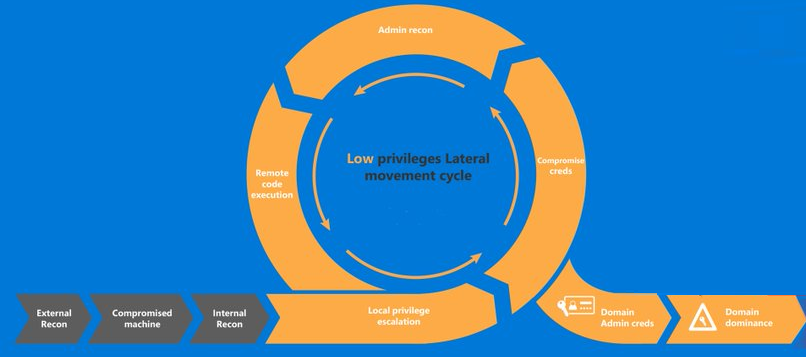
How does Pentesting of Active Directory Work?
- Pre-engagement Interactions: This is the initial stage where the rules of engagement are decided. It also involves defining the scope and objectives of the pentest.
2. Intelligence Gathering: In this stage, the pentester gathers as much information about the AD environment as possible. This includes identifying the domain controllers, user accounts, and computer accounts.
3. Threat Modeling: Based on the intelligence gathered, the pentester identifies potential vulnerabilities in the AD environment.
4. Vulnerability Analysis: The pentester explores identified vulnerabilities, determining which ones can be exploited.
5. Exploitation: This stage involves attempting to exploit the identified vulnerabilities to gain unauthorized access to resources.
6. Post Exploitation: Upon successful exploitation, the pentester tries to maintain access and gather more information, escalating privileges where possible.
7. Reporting: Finally, a detailed report is created, outlining the vulnerabilities found, data exploited, and recommendations for remediation.
To effectively perform Active Directory pentesting, you need a suite of tools and techniques at your disposal. Some of the more common tools used include PowerSploit, BloodHound, and Nmap. A good understanding of PowerShell scripting is also beneficial. For a deeper understanding of how pentesting works in practice, refer to this HackerOne Blog post.
While pentesting is a crucial aspect of Active Directory security, it's only one part of a comprehensive cybersecurity strategy. In the subsequent sections, we'll discuss the security implications of Active Directory vulnerabilities and how to detect and prevent potential exploits. Stay tuned for more detailed insights.
Security Implications
Active Directory (AD) is a cornerstone of most enterprise networks, making it a prime target for cybercriminals. Understanding the security implications of penetration testing Active Directory (AD) is therefore critical in anticipating potential attack vectors.
Attack Vectors
The attack vectors related to AD penetration testing are vast and varied. They range from simple brute force attacks on weak passwords to sophisticated Golden Ticket attacks where an attacker obtains elevated privileges and then generates a Kerberos ticket granting ticket (TGT) for any account in the domain.
A common exploitation technique is the Pass-the-Hash (PtH) attack, where attackers steal the NTLM (NT LAN Manager) hashes instead of the plaintext passwords. The stolen hashes can then be used to authenticate to network resources, bypassing the need for the actual password. Our article on exploiting SMB vulnerabilities provides an excellent case study on how this technique can be used to compromise an entire network.
Real-World Examples
One real-world example of an AD-related security breach is the infamous SolarWinds attack. In this case, the attackers were able to compromise the SolarWinds Orion software and use it as a conduit to penetrate the networks of numerous high-profile victims. A detailed analysis is available on the HackerOne Blog.
Detection and Prevention
Detecting and preventing attacks on your AD environment requires a comprehensive approach that combines proactive measures with continuous monitoring.
Methods to Detect Exploitation
The first line of defense in detecting AD exploitation is through effective log management. Detailed logging and monitoring can reveal suspicious patterns of behavior, such as repeated failed login attempts or unusual account activity.
The second line of defense is anomaly detection. This involves the use of advanced statistical modeling techniques to identify unusual behavior that deviates from the norm. More information on these techniques can be found in our article on advanced threat hunting.
Defensive Strategies and Best Practices
Defensive strategies for AD range from basic measures such as enforcing strong passwords and regularly updating systems, to more advanced strategies like implementing least privilege access and segregating administrative duties. For a comprehensive guide on securing your AD environment, refer to our article on advanced Active Directory security best practices.
Advanced Topics
As attackers continue to evolve their tactics, so too must our defenses. This requires staying abreast of cutting-edge research and techniques in AD security.
Cutting-edge Research and Techniques
One promising area of research is the use of machine learning (ML) for detecting AD attacks. By training an ML model on normal AD behavior, it can potentially identify abnormal activity indicative of an attack. For more on this topic, consult the NIST Special Publications.
Conclusion
In conclusion, the importance of AD security cannot be overstated. By understanding the potential attack vectors, implementing robust defenses, and staying informed of the latest research, you can significantly enhance your organization's resilience against AD-related attacks.
For further learning and to stay updated on the latest developments in cybersecurity, revisit our blog regularly. Always remember, the key to effective cybersecurity is continual learning and adaptation.




