Embracing DevSecOps: Integrating Security into the DevOps Pipeline
Disclaimer
This article is intended solely for educational purposes. The techniques described here should only be tested in controlled and authorized environments. Unauthorized use of these methods is illegal and unethical. Always adhere to legal and ethical guidelines when conducting security practices.
Embracing DevSecOps: Integrating Security into the DevOps Pipeline
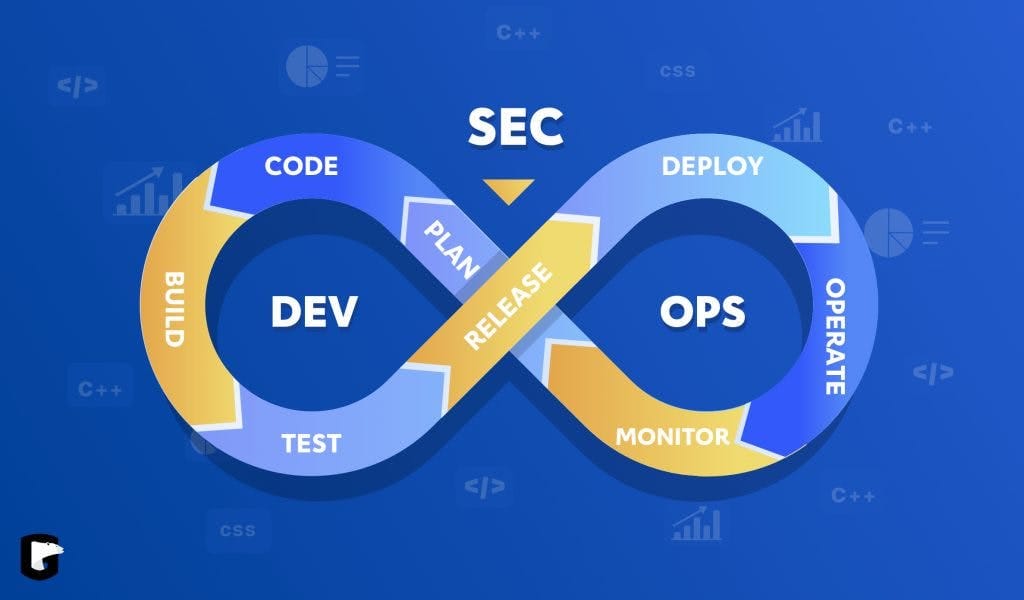
As organizations accelerate their software delivery processes with DevOps, security often becomes an afterthought. This gap has led to the rise of DevSecOps—a paradigm that embeds security practices directly into the DevOps pipeline.
Instead of considering security as a final step, DevSecOps aims to integrate security throughout the entire development lifecycle, from planning and coding to deployment and monitoring. In this article, we will explore the core concepts of DevSecOps, best practices, popular tools, and how to implement a robust DevSecOps strategy.
What is DevSecOps?
Keyword: DevSecOps Practices
DevSecOps stands for Development, Security, and Operations. It’s an evolution of DevOps where security is treated as a shared responsibility throughout the entire IT lifecycle. This approach allows teams to detect and fix security issues as early as possible, rather than addressing them after deployment.
Core Principles of DevSecOps:
1. Shift-Left Security: Integrate security early in the development process.
2. Automation: Automate security checks and tests within CI/CD pipelines.
3. Collaboration: Foster collaboration between development, security, and operations teams.
4. Continuous Monitoring: Monitor applications and infrastructure continuously to detect threats in real-time.
5. Infrastructure as Code (IaC): Manage infrastructure using code to ensure consistency and security.
Why DevSecOps Matters
Keyword: Benefits of DevSecOps
Traditional security approaches often fail to keep up with the fast-paced, iterative nature of DevOps. DevSecOps addresses this gap by:
• Reducing Security Vulnerabilities Early: Catching issues during development rather than in production.
• Minimizing Remediation Costs: Fixing bugs in production is significantly more expensive than addressing them during development.
• Enhancing Collaboration: Encouraging communication between developers, security experts, and operations teams.
• Improving Compliance: Automating security tests helps maintain regulatory compliance.
Key Practices for Implementing DevSecOps
1. Integrate Security into CI/CD Pipelines
Automate security testing as part of the Continuous Integration and Continuous Deployment (CI/CD) process. Include the following steps:
• Static Application Security Testing (SAST): Analyze source code for vulnerabilities before building.
• Dynamic Application Security Testing (DAST): Simulate attacks on running applications.
• Software Composition Analysis (SCA): Detect vulnerabilities in third-party libraries.
• Container Security Scanning: Identify issues in Docker images and Kubernetes configurations.
Example Tools:
• Jenkins: Automate security checks in CI/CD.
• GitLab CI: Integrate security scans as pipeline stages.
• SonarQube: Perform static code analysis.
• OWASP ZAP: Conduct dynamic analysis of web applications.
2. Infrastructure as Code (IaC) Security
Keyword: Securing Infrastructure as Code
Managing infrastructure through code (e.g., Terraform, Ansible) introduces new security challenges. Apply security policies at the code level to prevent misconfigurations.
Best Practices:
• Code Scanning: Use tools like TFLint and Terraform Validator to detect insecure configurations.
• Policy Enforcement: Automate compliance checks using Open Policy Agent (OPA).
• Configuration Management: Track all changes using version control (e.g., Git).
3. Automated Security Testing
Embed security testing in every stage of the pipeline to ensure early detection and remediation.
Techniques:
• Unit Testing with Security in Mind: Test for input validation and data sanitization.
• Penetration Testing Automation: Integrate tools like Burp Suite and Nikto for automated vulnerability assessments.
• Fuzz Testing: Generate random input data to detect crashes and vulnerabilities.
4. Container and Microservices Security
Keyword: Securing Containers in DevSecOps
Containers and microservices introduce unique challenges related to isolation and scalability. Secure your containerized environments by:
• Scanning Docker Images: Use tools like Clair and Trivy to detect vulnerabilities.
• Runtime Monitoring: Monitor container behavior with Falco.
• Kubernetes Security: Implement Pod Security Policies (PSP) and network segmentation.
Example Workflow:
1. Build: Create container images and scan for vulnerabilities.
2. Deploy: Enforce security policies and deploy in a secure Kubernetes environment.
3. Monitor: Continuously monitor for runtime anomalies and threats.
5. Continuous Monitoring and Threat Detection
After deployment, maintain security through continuous monitoring:
• Log Aggregation and Analysis: Use ELK Stack (Elasticsearch, Logstash, Kibana) to aggregate and visualize logs.
• Intrusion Detection Systems (IDS): Deploy Wazuh or OSSEC to detect suspicious activity.
• Behavioral Analytics: Implement anomaly detection using tools like Splunk.
Popular Tools in the DevSecOps Ecosystem
1. SonarQube: Code quality and vulnerability analysis.
2. Trivy: Container vulnerability scanning.
3. OWASP ZAP: Dynamic application security testing.
4. Clair: Static analysis of vulnerabilities in containers.
5. Sysdig Falco: Real-time threat detection for containers.
6. Terraform Validator: Infrastructure compliance checks.
7. Aqua Security: Container security monitoring.
8. GitLab CI/CD: Automates DevSecOps pipelines.
Challenges and How to Overcome Them
1. Resistance to Change: Educate teams about the importance of security integration.
2. Tool Overload: Choose a limited set of tools that fit your ecosystem.
3. Skill Gaps: Train developers and operations teams on secure coding practices and tool usage.
4. Performance Issues: Integrate security checks that minimize build time and optimize performance.
Best Practices for Successful DevSecOps Implementation
1. Automate Everything: Automate code analysis, testing, and monitoring.
2. Empower Developers: Give developers the tools and training to write secure code.
3. Adopt a Shift-Left Mindset: Address security from the start of the development process.
4. Collaborate Cross-Functionally: Ensure developers, security experts, and operations collaborate effectively.
5. Measure and Improve: Continuously assess security metrics and refine processes.
Conclusion
Adopting DevSecOps is essential for organizations aiming to deliver secure software at speed. By integrating security into every phase of the CI/CD pipeline, teams can reduce vulnerabilities and respond faster to emerging threats. Embracing a security-first mindset while maintaining agile practices ensures that both security and innovation coexist harmoniously.




