PingCastle: Complete Guide to Active Directory Security Auditing
In the realm of Active Directory (AD) security, detecting vulnerabilities and misconfigurations is crucial to maintaining a robust defense against cyberattacks. One of the most effective tools for auditing and analyzing AD security is PingCastle.
PingCastle is a powerful, free, and lightweight tool designed to perform comprehensive security audits on Active Directory environments. In this guide, we’ll dive deep into how to use PingCastle for AD auditing, its key features, practical implementation, and best practices to secure your infrastructure.
What is PingCastle?
Keyword: PingCastle Active Directory Audit
PingCastle is an open-source tool developed to assess the security health of Active Directory domains. It provides a comprehensive report on potential vulnerabilities and misconfigurations that could expose your environment to attacks.
Key Features:
- Health Check Report: Generates a detailed security assessment.
- Risk Level Assessment: Provides a security score and risk level.
- Detection of Misconfigurations: Identifies weak configurations and risky practices.
- Privilege Escalation Detection: Reveals potential paths to domain admin.
- Historical Analysis: Tracks changes and improvements over time.
Why Use PingCastle for AD Auditing?
Keyword: Benefits of Using PingCastle
Organizations often overlook their Active Directory security posture, leaving them vulnerable to attacks like Kerberoasting, Pass-the-Hash, and Golden Ticket attacks. PingCastle addresses these challenges by:
- Automating Audits: Quickly performing thorough AD security checks.
- Identifying High-Risk Configurations: Detecting issues before attackers exploit them.
- Generating Actionable Reports: Offering clear remediation guidance.
- Tracking Improvements: Monitoring progress over time.
Step 1: Download and Install PingCastle
Keyword: PingCastle Installation
PingCastle is a portable tool, meaning it doesn't require installation. You can run it directly from any Windows system with domain access.
Download PingCastle:
- Visit the PingCastle official website:
PingCastle Download - Download the latest version in a .zip format.
- Extract the archive to a suitable location on your machine.
Step 2: Running Your First AD Audit
Keyword: PingCastle AD Audit
To perform your first audit, open a Command Prompt with administrative privileges and navigate to the PingCastle directory.
Health Check Command:
PingCastle.exe --healthcheck
Advanced Health Check (with Domain Specification):
PingCastle.exe --healthcheck --server mydomain.local
Understanding the Health Check Report
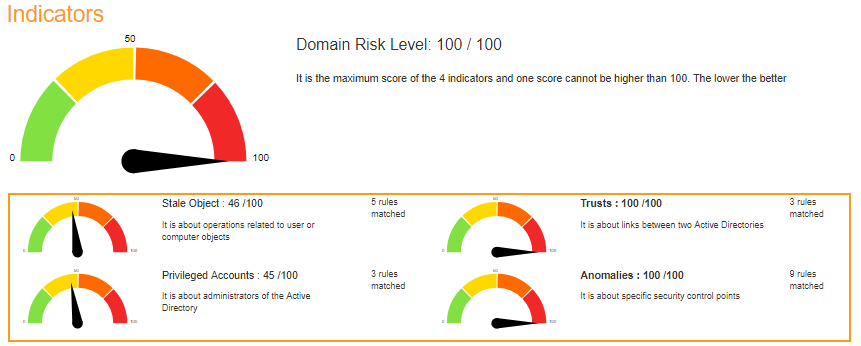
The Health Check report contains several critical components:
- Global Score: An overall security score ranging from 0 (critical) to 100 (secure).
- Risk Levels: Identifies risk areas (e.g., user account security, password policies).
- Recommendations: Suggested remediations for each detected issue.
- Criticality Map: Graphically displays the most critical vulnerabilities.
- Privilege Escalation Paths: Shows potential paths to domain admin privileges.
Analyzing the Global Score:
The global score is an aggregated rating that reflects the overall security posture of the AD environment.
- Score 90-100: Excellent security posture
- Score 70-89: Good, but minor improvements needed
- Score 50-69: Moderate risk, improvements recommended
- Score below 50: High risk, urgent remediation required
Step 3: Interpreting Critical Findings
1. Weak Password Policies
Keyword: Active Directory Password Security
PingCastle often flags weak password policies as a major risk. To enhance password security:
- Enforce Complexity: Use combinations of uppercase, lowercase, numbers, and symbols.
- Minimum Length: Set a length of at least 12-16 characters.
- Expiration Policies: Implement regular password changes.
GPO Settings:
Go to Group Policy Management Console (GPMC):
Computer Configuration -> Policies -> Windows Settings -> Security Settings -> Account Policies -> Password Policy2. Unconstrained Delegation Risks
Keyword: Unconstrained Delegation Vulnerability
Unconstrained delegation allows any service to impersonate a user. Attackers can use tools like Mimikatz to abuse this configuration and escalate privileges.
How to Fix:
- Disable Unnecessary Delegation:
Get-ADComputer -Filter {TrustedForDelegation -eq $true}
- Implement Constrained Delegation: Limit delegation to specific services.
3. Privileged Account Misconfigurations
Keyword: Active Directory Privileged Accounts
PingCastle identifies privileged accounts that are susceptible to misuse or compromise.
- Principle of Least Privilege (PoLP): Restrict admin rights to essential accounts only.
- Monitor Privileged Logins: Track privileged user activities.
Remediation:
Review privileged accounts using PowerShell:
Get-ADGroupMember -Identity "Domain Admins" -Recursive
4. Kerberos Configuration Issues
Keyword: Kerberos Security Best Practices
Misconfigured Kerberos settings can lead to Golden Ticket attacks.
- Enable AES Encryption: Use AES256 for ticket encryption.
- Reduce Ticket Lifetime: Decrease the Maximum Lifetime for User Tickets to 4 hours.
Configure via Group Policy:
Computer Configuration -> Policies -> Windows Settings -> Security Settings -> Account Policies -> Kerberos PolicyStep 4: Reporting and Tracking Improvements
PingCastle allows you to export reports in various formats:
PingCastle.exe --healthcheck --export-pdf
Use these reports to:
- Share with Stakeholders: Provide comprehensive security insights.
- Monitor Progress: Compare scores over time to measure improvements.
- Guide Remediation Efforts: Implement fixes systematically based on criticality.
Step 5: Automating PingCastle Audits
Keyword: Automating AD Audits with PingCastle
Automate regular audits using Task Scheduler:
- Open Task Scheduler.
- Create a new task with administrative privileges.
- Set the trigger to run at desired intervals (e.g., weekly).
- Configure the action to run the PingCastle health check command.
Best Practices for Active Directory Security Using PingCastle
- Schedule Regular Audits: Automate health checks and compare reports.
- Monitor Privileged Accounts: Use PingCastle to continuously track privileged changes.
- Harden Configuration Settings: Follow recommendations to reduce risk.
- Integrate with SIEM Tools: Use Wazuh or Splunk to monitor and correlate results.
- Educate Your Team: Train administrators on how to interpret and act on PingCastle reports.
Conclusion
PingCastle is a robust tool that enables organizations to maintain a secure and resilient Active Directory environment. Its comprehensive auditing and reporting capabilities make it an essential tool for any SOC or IT security team.
By leveraging PingCastle regularly and following the best practices outlined in this guide, you can significantly reduce the attack surface of your Active Directory infrastructure.




