Advanced Phishing Detection Beyond Email: Defending Against Multi-Channel Social Engineering
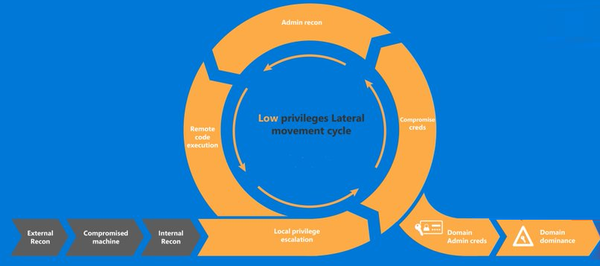
The evolution of phishing attacks represents one of the most significant shifts in the threat landscape over the past decade. No longer confined to poorly crafted emails with suspicious attachments, today's social engineering attacks have evolved into sophisticated, multi-channel campaigns that target users across email, SMS, voice calls,